Forensic Investigation: Examining Corrupted File Extension
In this article, we will learn how we can Examine Corrupted File Extension to identify the basic file header in a Forensic Investigation.
Let’s understand this with the following Scenario
In this Scenario, a forensic investigator has gone for an investigation and found out a suspicious folder where no file has any kind of file extension. Now, what will he do to proceed in his forensic investigation?
Objective: Learn to use various techniques in Forensic Investigation to analyse and examine the various file headers
- Examining Corrupted File Extension using Windows Platform.
- Examining Corrupted File Extension using Linux Platform.
Table of Content
Cheatsheet for Hex File Header
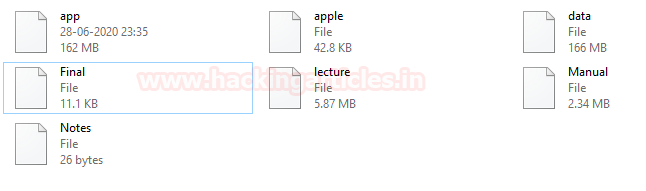
Examining Corrupted File Extension using Windows Platform
- File #1: app
- File #2: apple
- File #3: data
- File #4: Final
- File #5: lecture
- File #6: Manual
- File #7: Notes
- Recovered all files successfully
Examining Corrupted File Extension using Linux Platform
- Analyze in Linux with file command
- Analyze in Linux
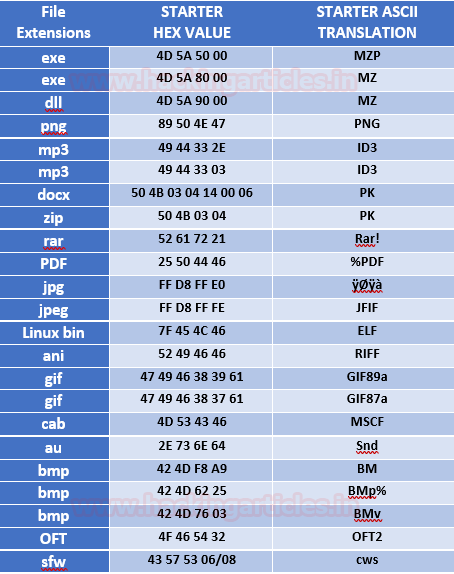
Cheatsheet for Hex File Header
We all know that the hex file header is used to identify any file by examining the first 4 or 5 bytes of its hexadecimal content.
We have created our very own cheat sheet to examine these values more appropriately; Which contains all the basic files extensions and its 4 to 5 bytes starter hexadecimal value along with its ASCII translation.
Examining Corrupted File Extension using Windows Platform
As per the given scenario, the first thing which comes into our mind that let’s check these files in the command prompt [cmd]. Nevertheless, nothing is visible to the investigator.
Now Let’s try to examine each file we found this folder and try to restore them in their original format.
File #1: app
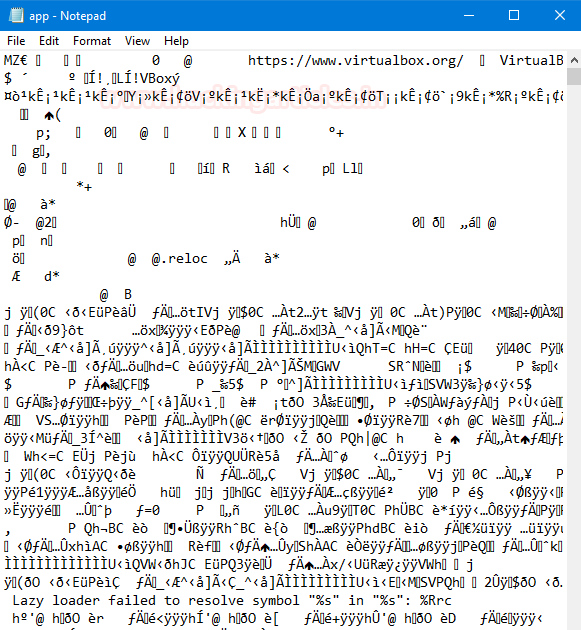
The first file, which we got is app. The first thing that comes into our mind is to open this file with the help of notepad. We are doing it to show you guys that the file is in an unreadable format.
Now, we examine hexadecimal values of these files with Hexadecimal editor. We can use any kind of hexadecimal editor, that can show us a hexadecimal value of any file. After opening that file, we need to examine its stating hexadecimal value to know about the file type.
So, I have used Hex Workshop which you can download from here.
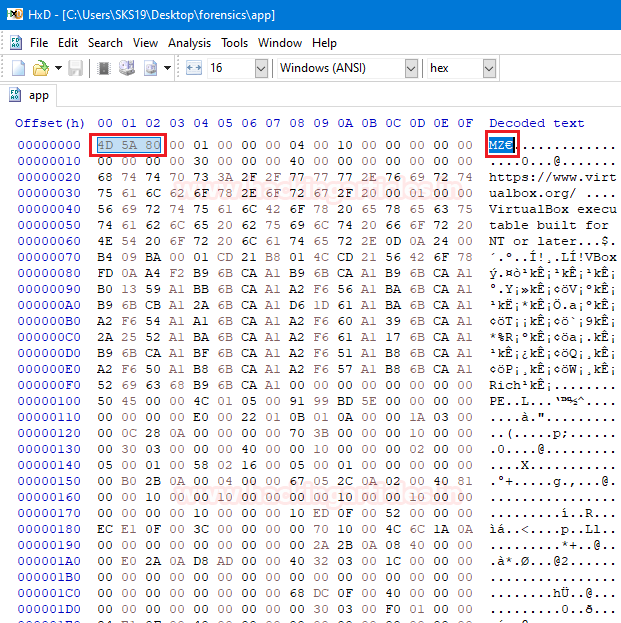
After, analyzing its starting bytes with our cheat sheet. We come to know that it is a .exe file with its ASCII translation MZ. MZ is the initials of Mark Zbikowski, he is the designer of the DOS executable file format. We have successfully investigated the first file as a .exe file.
Now, we have two methods to rename that file extension.
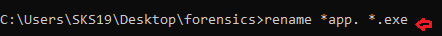
Method 1: With the help of the command line.
Follow this command to rename this file extension.
rename *app. *.exe
This command helps us to select only the app file to rename only this file extension. Because others are yet to be examined.
Method 2: We can simply change it directly by renaming the file name and providing it with an extension which we already find above.
File #2: apple
Now, it’s time to examine the second file all we know about that file is its name apple. Straight away we opened that file in the hexadecimal editor. To start analyzing its hexadecimal values.
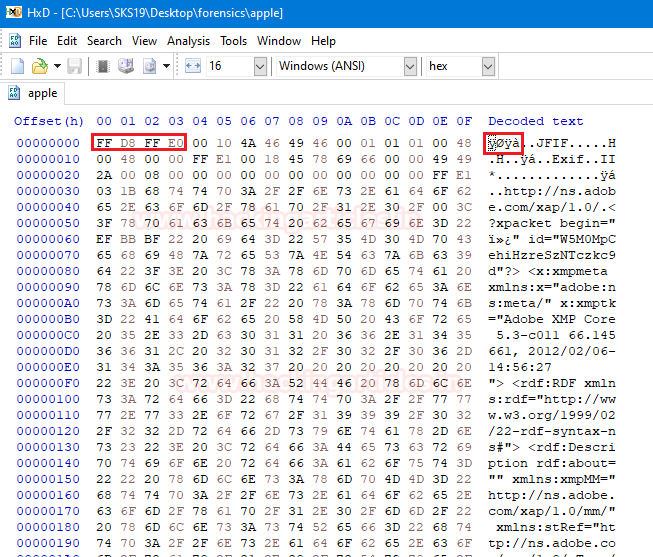
As we have to try to match its starting 4 bytes with our cheat sheet. We were quickly able to find out it is a .jpg file with ASCII translation ÿØÿà.
Now, just rename this file with the help of this command.
rename *apple. *.jpg
This command will only change the apple file to a .jpg file. Because others are yet to be examined.
File #3: data
Time to examine the third file which name is data. We are opening that file into a hexadecimal editor, to examine its hexadecimal values.
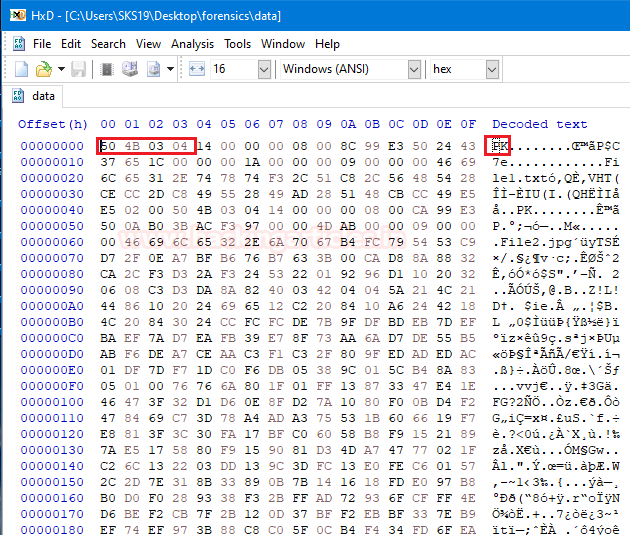
Now, try to match it first 4 bytes with our cheat sheet which we provide above. In a few moments, we find out that it is a .zip file with ASCII translation PK.
Change the file name and provide it with an extension with the help of rename command.
rename *data. *.zip
As we know it will only make changes in data and change it into a .zip file.

File #4: Final
Here comes the fourth file which name is Final. Now, open that file in a hexadecimal editor to analyse its hexadecimal values.
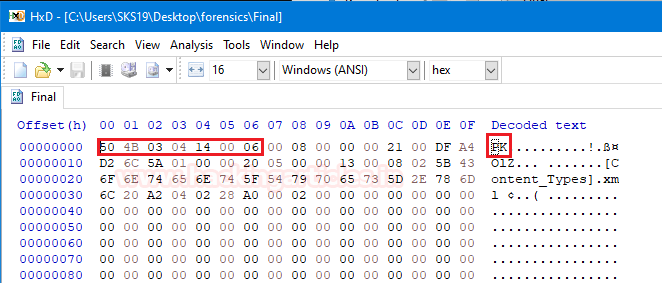
After opening that file, try to match its first seven bytes with our cheat sheet. In a few moments, we found out that its values match with a .docx file. So, it is a .docx file with ASCII translation PK.
Just change its name and provide it with a .docx extension with the help of [rename] command.
rename *Final. *.docx
File #5: lecture
The fifth file named as a lecture; we try to open that file in a hexadecimal editor. To analyse its hexadecimal values, which helps us to identify its file type.
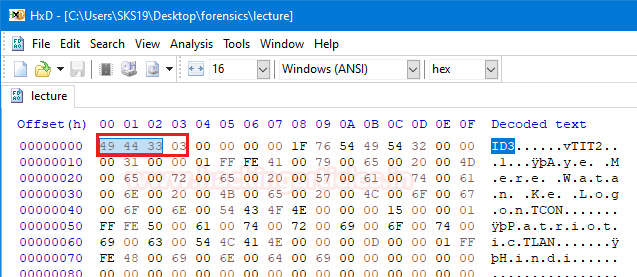
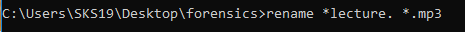
Now, try to match its first four bytes. In a moment we found out that it is a .mp3 file with an ASCII translation ID3. Just provide that file a .mp3 extension with the help of [rename] command.
rename *lecture. *.mp3
File #6: Manual
The second last file in that folder named Manual. Open that file in a hexadecimal editor to examine its hexadecimal values.
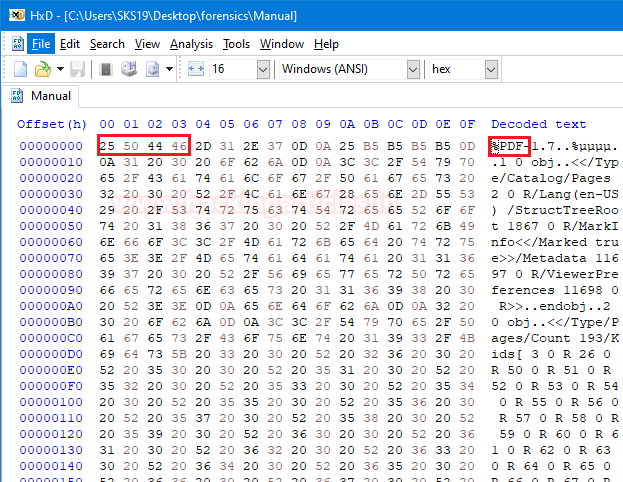
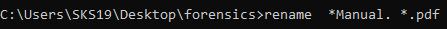
Now, try to match its four bytes with our cheat sheet. Then we come to know that it is a .pdf file with ASCII translation %PDF. Change its name and provide .pdf extension to it, with the help of rename command.
rename *Manual. *.pdf
File #7: Notes
Finally, we have reached to the file in the folder named Notes. Straight away we opened that file in a Hexadecimal editor to examine its hexadecimal values.
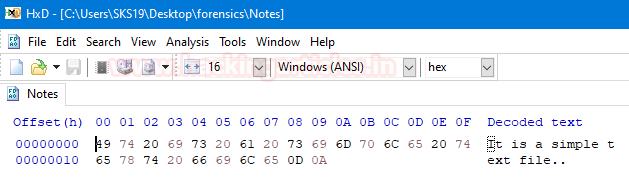
After opening it is saying that “It is a simple text file.”. so, we provided a .txt extension with the help of [rename] command.
rename *Notes. *.txt
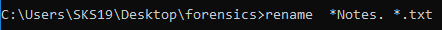
Recovered all File successfully
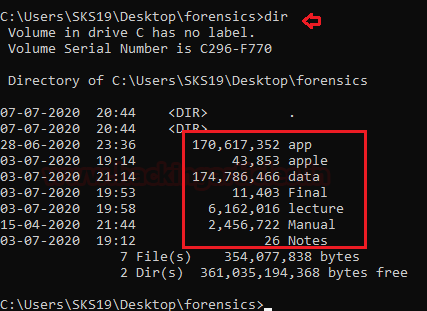
Now, look at the folder which itself saying that we have recovered all the files successfully.
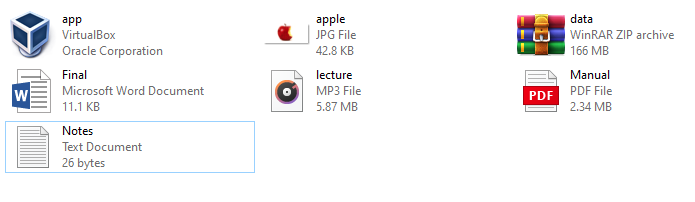
And we can also see that these files were recovered in the command prompt along with its original extension, with the help of [dir] command.
Examining Corrupted File Extension using Linux Platform
Now suppose in your investigation, you are in the same scenario where the file extension is missing but this time the Victim machine operates on Linux Environment and you are not allowed to copy this folder on another machine. Then How would you handle this situation?
Analysis using the File command
The file command is a Linux utility that analyzes each argument in an attempt to classify it. Hence, we can examine this forensic investigation in a Linux environment with the help of file command.
We are using the [ls] command to show you guys, these are the same files and the same scenario that we already explained above.
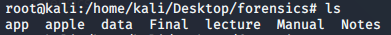
We just need to use [file] along with the file name, to know about the originality of that file. Pick the first file and use this command. It shows that it is an MS Windows executable file.
file app
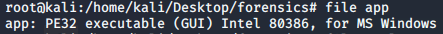
Let us try the same technique with the second file named apple. Apply [file] command and provide its file name. It shows that it is a jpeg image along with its internal pieces of information.
file apple
This article will help us to identify the true identity of a file during a Forensic Investigation in both the Windows and Linux environments.
Author: Shubham Sharma is a Pentester and Cybersecurity Researcher, Contact Linkedin and twitter.
Thanks Raj.
I have seen that you are posting more forensics lab! These labs are very helpful.
Thank you for the great work you have done.
As a beginner in the field of computer forensics, I appreciate it. I have a question do you give classes online. I will appreciate it.
yes we are providing Online Training Kindly Contact info@ignitetechnologies.in